Fingerprinting STAR-ECHO
║▌║▌│█║▌║│█│█║║║▌║
$ fingerprint@info:~ echo $STAR-ECHO-
Name:
STAR-ECHO
Original feature purpose:
--- (considered as a bug)
FP-Explanation:
Web browsers allow to load resources from private IP addresses (10.0.0.0 – 10.255.255.255/172.16.0.0 – 172.31.255.255/192.168.0.0 – 192.168.255.255). Thus, it is possible to ascertain if specific software is used by the client. Loading local resources also exposes information about the router (vendor/version) the client is connected to or VPN network/provider information, IoT devices in the same network, NAS services, media/stream server and anything else that is accessible via http from the client's system.
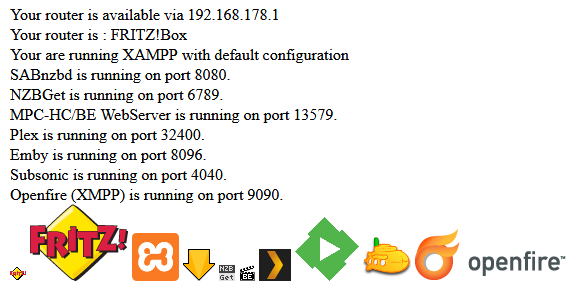
Extracted information (exemplary cases):- Your router is available via 192.168.178.1
- Your router is: FRITZ!Box
- Your FRITZ!Box has NAS support
- Your FRITZ!Box has NAS support on FRITZ!OS 06.30* < FRITZ!OS 07.01
- Your FRITZ!Box has MESH support (FRITZ!OS > 07.01)
- You have FRITZ!Box 7360
- You have FRITZ!Box 7272
- You have FRITZ!Box 7170
- You have FRITZ!Box Fon WLAN
- You are running XAMPP with default configuration
- You are running a server on localhost
- You are running a server and VirtualBox Host-Only Network is enabled
- SABnzbd is running on port 8080
- SABnzbd is running on port 8082
- NZBGet is running on port 6789
- MPC-HC/BE WebServer is running on port 13579
- Plex is running on port 32400
- Emby is running on port 8096
- Subsonic is running on port 4040
- Openfire (XMPP) is running on port 9090
- You are connected to a Vodafone-Hotspot
- You are connected to a SWM-Hotspot
- You are connected to MWN
The demo implementation is currently active fingerprinting.
Passive fingerprinting can be done as well. For example with the CSS pseudo element ":after" as shown here:
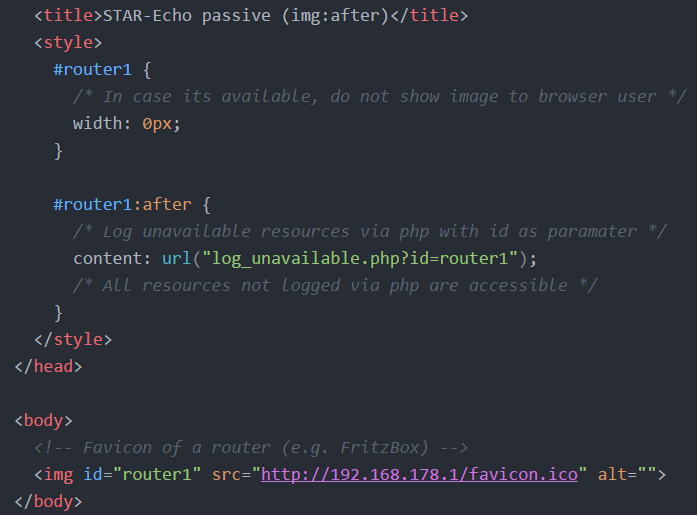
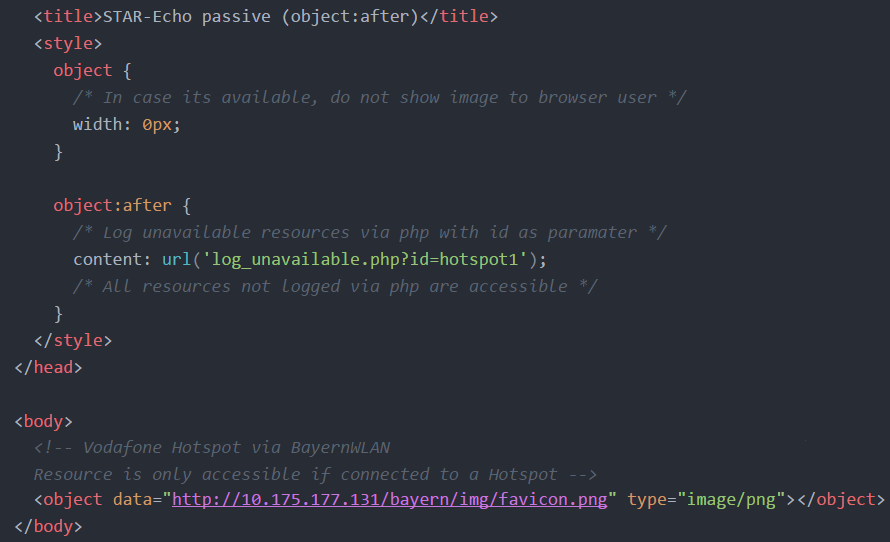
If resources are tested without a ?timecode URL-appendix to prevent accessing a cached-version, it is possible to extract local connection information made in the past.
FP-Type:
active
FP-Categories:
js, hardware-dependent, software-dependent, unchanged-consistent, short-living, cross-browser
Counter-measures:
-
Block/request permission for local resource requests via browser settings or addon
Problem: No browser has implemented this feature yet (Jan, 2019)
-
Block local resource requests by system firewall
Explanation: Local resources will not be loaded within the browser and websites will not be informed which servers are running on your system and in your network. -
Use proxy to block local requests
Explanation: Configure, e.g., a SOCKS v5 on your system mapped to 127.0.0.1:1080 -
Change default server ports
Explanation: The script must loop through ports to detect if a server is running
Problem: If the script detects your choosen port, this makes you stand out more
Publications/References:
- A privacy by design browser solution as protection against personalized online tracking (2019)
- STAR-ECHO (Servers That Are Running-Echo) - What is running? (GitHub Pages)
- STAR-ECHO (Servers That Are Running-Echo) - What is running? (JSFiddle)
- Exposed local server information and local ips (Bugzilla)
$ fingerprint@info:~ run star-echo-demo
Demo:
>> Jump to STAR-ECHO Fingerprinting Demo <<Your STAR-Echo Output:
Example output: